In this tutorial we will make use of free ssl certificate provided by Lets Encrypt to make website secure by enabling HTTPS. We will install certificate provided by lets encrypt using EFF's certbot client.
Steps to Install Let's Encrypt's Free SSL Certificates
- Prerequisites
Before proceeding with this tutorial we assume that you have successfully setup website on google cloud and website is accessible via domain. We also assume that you can ssh your cloud vm either from web browser using google cloud console or by configuring public key based ssh connection from local machine.
- Enable HTTPS for Google Cloud VM
Open Google Compute Engine Instance and Select Edit to enable
HTTPStraffic.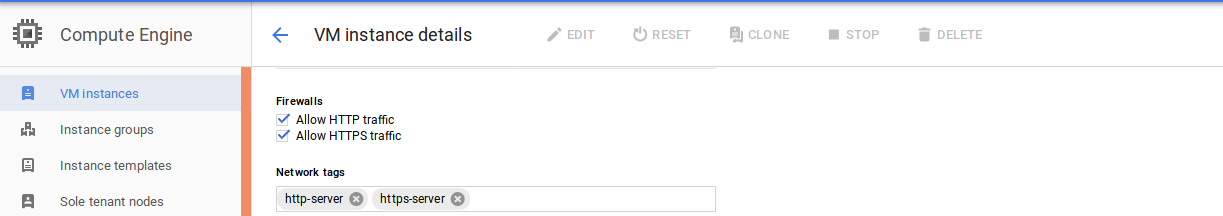
Enable HTTPS - Firewall Rule This will create firewall rule to open port
443on compute instance and facilitate serving of HTTPS request after certificate installation.
- SSH Google Cloud VM
SSH to cloud vm from from your local machine.
techmonger@ubuntu:~$ ssh 93.184.216.34 The programs included with the Debian GNU/Linux system are free software; the exact distribution terms for each program are described in the individual files in /usr/share/doc/*/copyright. Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent permitted by applicable law. techmonger@google-vm:~$ - Backup Apache Configuration Files
Before proceeding with certificate installation, it is important to have backup of existing Webserver configuration files. Certificate installation program will modify configuration file during certificate installation. Backing up existing configuration file will give us opportunity to restore old configuration back if anything is not working as expected after certificate installation.
$ mkdir /tmp/apache_config_backup/ $ cp -r /etc/apache2/* /tmp/apache_config_backup/ - Install Certbot Client
We have created VM instance with Debian OS and will use following commands to install certbot client. However if you have some other OS for your VM then please follow instructions at
https://certbot.eff.orgto install certbot.$ sudo apt-get install python-certbot-apache -t stretch-backports - Install Certificates with Certbot for Apache
Initiate Certificate Installation Program
$ sudo certbot --authenticator webroot --installer apache Saving debug log to /var/log/letsencrypt/letsencrypt.log Plugins selected: Authenticator webroot, Installer apacheProvide valid Email Address
Enter email address (used for urgent renewal and security notices) (Enter 'c' to cancel): techmonger@example.comAccept (A) Let's Encrypt Terms and Conditions
Please read the Terms of Service at https://letsencrypt.org/documents/LE-SA-v1.2-November-15-2017.pdf. You must agree in order to register with the ACME server at https://acme-v01.api.letsencrypt.org/directory (A)gree/(C)ancel: AOption to Share Email with EFF. Select (Y/N) depending on your preferences.
Would you be willing to share your email address with the Electronic Frontier Foundation, a founding partner of the Let's Encrypt project and the non-profit organization that develops Certbot? We'd like to send you email about our work encrypting the web, EFF news, campaigns, and ways to support digital freedom. (Y)es/(N)o: YDomain name to install certificate for. (
example.com)No names were found in your configuration files. Please enter in your domain name(s) (comma and/or space separated) (Enter 'c' to cancel): example.com Obtaining a new certificate Performing the following challenges: http-01 challenge for example.comWeb Server root where website content is stored and accessible.(
/var/www/html)Input the webroot for example.com: (Enter 'c' to cancel): /var/www/html Waiting for verification... Cleaning up challenges Created an SSL vhost at /etc/apache2/sites-available/000-default-le-ssl.conf Enabled Apache socache_shmcb module Enabled Apache ssl module Deploying Certificate to VirtualHost /etc/apache2/sites-available/000-default-le-ssl.conf Enabling available site: /etc/apache2/sites-available/000-default-le-ssl.confOption To configure
HTTPtoHTTPSredirect. Select 1 or 2 depending on whether or not you want to configure redirect.Please choose whether or not to redirect HTTP traffic to HTTPS, removing HTTP access. ----------------------------------------------------- 1: No redirect - Make no further changes to the webserver configuration. 2: Redirect - Make all requests redirect to secure HTTPS access. Choose this for new sites, or if you're confident your site works on HTTPS You can undo this change by editing your web server's configuration. ----------------------------------------------------- Select the appropriate number [1-2] then [enter] (press 'c' to cancel): 2 Enabled Apache rewrite module Redirecting vhost in /etc/apache2/sites-enabled/000-default.conf to ssl vhost in /etc/apache2/sites-available/000-default-le-ssl.conf -----------------------------------------------------Message for Successful Configuration
Congratulations! You have successfully enabled https:/example.com You should test your configuration at: https://www.ssllabs.com/ssltest/analyze.html?d=example.comDetails about certificate files
IMPORTANT NOTES: - Congratulations! Your certificate and chain have been saved at: /etc/letsencrypt/live/example.com/fullchain.pem Your key file has been saved at: /etc/letsencrypt/live/example.com/privkey.pem Your cert will expire on 2018-09-10. To obtain a new or tweaked version of this certificate in the future, simply run certbot again with the "certonly" option. To non-interactively renew *all* of your certificates, run "certbot renew" - Your account credentials have been saved in your Certbot configuration directory at /etc/letsencrypt. You should make a secure backup of this folder now. This configuration directory will also contain certificates and private keys obtained by Certbot so making regular backups of this folder is ideal. - If you like Certbot, please consider supporting our work by: Donating to ISRG / Let's Encrypt: https://letsencrypt.org/donate Donating to EFF:https://eff.org/donate-le
- Test HTTPS Connection
Open website domain in web browser with
HTTPSand ensure that website is working as expected. If redirect is configured then checkHTTPtoHTTPSredirect for webisite pages by opening pages withHTTPin browser.
- Auto Renewal of Certificates
By default let's encrypt certificates would expire after 90 days of installation. It is important to have an automated way to renew certificate before expiry date. Certbot does this for you by creating a cron job. Learn more about how certbot auto renew certificates works.
Conclusion
We have installed free Lets encrypt SSL certificates for the static website hosted on google cloud vm. These certificates have been configured for Apache webserver using Certbot client. We have also setup auto renewal of certificates to avoid manual renewal and certificate expiry.